
“Cybersecurity: Essential Steps to Protect Your Personal Data
Related Articles Cybersecurity: Essential Steps to Protect Your Personal Data
- What Is Big Data And How Does It Impact Business?
- The Impact Of Artificial Intelligence On Industry Transformation: A New Era Of Efficiency And Innovation
- The Evolution Of Computer Technology: From Mainframes To Cloud Computing
- Wearable Technology: Bringing Innovation To Health And Fitness
- The Advancements In Cloud Technology: Benefits And Challenges
Introduction
On this special occasion, we are happy to review interesting topics related to Cybersecurity: Essential Steps to Protect Your Personal Data. Let’s knit interesting information and provide new insights to readers.
Cybersecurity: Essential Steps to Protect Your Personal Data
In today’s hyper-connected world, our personal data is more valuable than ever, fueling everything from targeted advertising to sophisticated identity theft. A single data breach can unravel years of careful financial planning, erode trust, and even lead to significant emotional distress. The reality is, we’re all potential targets, regardless of our technological expertise. This article serves as a practical guide, outlining essential cybersecurity steps you can take to protect your personal information and maintain control over your digital life. We’ll move beyond generic advice, delving into specific strategies and actionable steps you can implement immediately to bolster your online defenses. Understanding and proactively managing your cybersecurity is no longer a luxury; it’s a necessity.
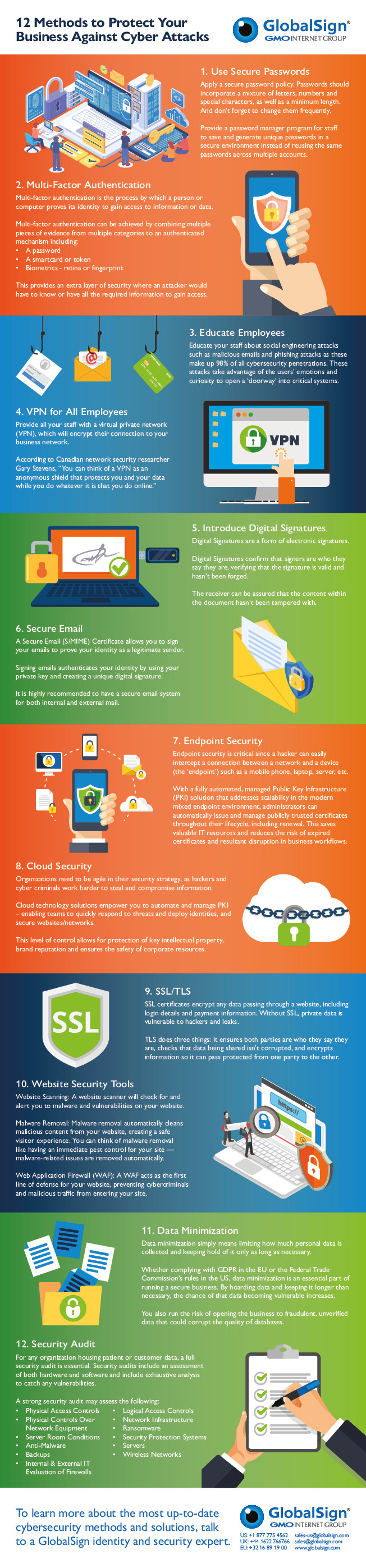
Strong Passwords: The Foundation of Digital Security
The cornerstone of any robust cybersecurity strategy is a strong, unique password for every online account. Reusing passwords is a catastrophic mistake; if one account is compromised, all your accounts are vulnerable. Instead, aim for passwords that are long (at least 12 characters), complex (combining uppercase and lowercase letters, numbers, and symbols), and unpredictable. Avoid using personal information like birthdays or pet names. Password managers, like LastPass, 1Password, or Bitwarden, can significantly simplify this process by securely generating and storing your passwords, eliminating the need to remember them all. Consider enabling multi-factor authentication (MFA) wherever possible, adding an extra layer of security beyond just a password. This often involves receiving a code via text message or authenticator app to verify your identity.
Software Updates: Patching the Vulnerabilities
Software developers constantly release updates to address security flaws and vulnerabilities. Ignoring these updates leaves your devices exposed to malware and hackers. Enable automatic updates on your operating system, web browser, and all other software whenever possible. This ensures that your systems are always running the latest, most secure versions. Regularly checking for updates manually is also a good practice, especially for applications that might not have automatic updates enabled. The infamous WannaCry ransomware attack in 2017, which crippled hospitals and businesses worldwide, highlighted the devastating consequences of neglecting software updates.
Phishing Awareness: Recognizing and Avoiding Traps
Phishing attacks remain one of the most prevalent cybersecurity threats. These scams involve deceptive emails, text messages, or websites designed to trick you into revealing sensitive information like passwords, credit card details, or social security numbers. Be wary of unsolicited emails or messages requesting personal information. Legitimate organizations rarely ask for such details via email. Always verify the sender’s identity by checking the email address and website URL carefully. Hovering your mouse over links before clicking can reveal the actual destination URL. Look for grammatical errors, suspicious links, and urgent or threatening language, all common indicators of a phishing attempt. Regularly educate yourself on the latest phishing tactics to stay ahead of the curve.
Secure Wi-Fi Networks: Protecting Your Connection
Public Wi-Fi networks, while convenient, are notoriously insecure. Using these networks exposes your data to potential eavesdropping and man-in-the-middle attacks. Avoid accessing sensitive information, like online banking or email, on public Wi-Fi. If you must use a public network, consider using a virtual private network (VPN). A VPN encrypts your internet traffic, making it much harder for others to intercept your data. When connecting to a Wi-Fi network at home or work, ensure it’s password-protected and regularly update your router’s firmware to patch security vulnerabilities. Choosing a strong and unique Wi-Fi password is just as crucial as protecting your online accounts.
Data Backup and Recovery: Safeguarding Your Information

Losing your personal data can be catastrophic. Regularly backing up your important files to an external hard drive, cloud storage service, or other secure location is crucial. This safeguards your data against hardware failure, theft, or ransomware attacks. Consider using a cloud storage service with robust encryption and security features. Implement a regular backup schedule to ensure that your data is consistently protected. Additionally, familiarize yourself with your data recovery options in case of a disaster. Knowing how to restore your data from a backup can significantly reduce the impact of a data loss event.
Device Security: Protecting Your Physical Assets
Your physical devices are the entry points to your digital life. Protect your devices with strong passwords, screen locks, and biometric authentication (fingerprint or facial recognition) whenever possible. Install reputable antivirus and anti-malware software and keep it updated. Be cautious about downloading apps from untrusted sources. Regularly review the permissions granted to apps on your devices, ensuring they only access the data they need. If you lose a device, report it immediately to your mobile carrier and any relevant authorities. Consider using a device tracking service to locate your lost device or remotely wipe its data.
Social Media Privacy: Managing Your Online Presence
Social media platforms often collect vast amounts of personal data. Review your privacy settings on all social media accounts and adjust them to limit the information shared publicly. Be mindful of the information you share online, avoiding oversharing personal details that could be used for identity theft or other malicious purposes. Think twice before accepting friend requests from strangers. Consider using a separate email address for social media accounts to protect your primary email from spam and phishing attempts. Regularly review your activity and connections to ensure your online presence aligns with your privacy preferences.

Email Security: Protecting Your Inbox
Email is a primary communication channel for many, making it a prime target for hackers. Be cautious of suspicious emails, especially those containing attachments or links from unknown senders. Avoid clicking on links or opening attachments from untrusted sources. Use strong and unique passwords for your email accounts and enable MFA. Regularly check your email account for any unauthorized access or suspicious activity. Consider using a spam filter to block unwanted emails and reduce the risk of phishing attacks.
Online Shopping Security: Protecting Your Transactions
Online shopping is incredibly convenient, but it also carries security risks. Only shop on secure websites that use HTTPS (look for the padlock icon in the address bar). Be cautious about entering your credit card information on unfamiliar websites. Consider using a virtual credit card or prepaid card for online purchases to limit your financial exposure. Check your bank and credit card statements regularly for unauthorized transactions. Report any suspicious activity immediately to your bank or credit card company.
Staying Informed: Continuous Learning and Adaptation

The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Stay informed about the latest threats and security best practices by following reputable cybersecurity news sources, participating in online forums, and attending cybersecurity awareness training sessions. Continuous learning is crucial to staying ahead of the curve and protecting yourself against emerging threats. Remember that even the most sophisticated security measures can be bypassed, so vigilance and awareness are paramount.
Conclusion
Protecting your personal data in the digital age requires a multi-faceted approach, encompassing strong passwords, regular software updates, phishing awareness, secure Wi-Fi practices, data backups, device security, social media privacy, email security, and safe online shopping habits. By implementing these essential steps, you significantly reduce your vulnerability to cyber threats and safeguard your valuable personal information. However, the fight against cybercrime is an ongoing battle. Staying informed, adapting to new threats, and maintaining a healthy dose of skepticism are crucial to ensuring your long-term digital security. The question isn’t if you’ll be targeted, but when. Are you prepared?
Conclusion
Thus, we hope this article has provided valuable insight into Cybersecurity: Essential Steps to Protect Your Personal Data. We appreciate your attention to our article. See you in our next article!






